Convert the following 32bit values to assembly code If the i
Convert the following 32-bit values to assembly code. If the instruction is a branch instruction, determine the address of the target using a starting of the file as 0x00400000. If the instruction is a jump type, determine the address of the target instruction. Identify any illegal or improperly formatted instruction.
Address
Instruction
Assembly Language Instruction
00400000
04CF1ED8
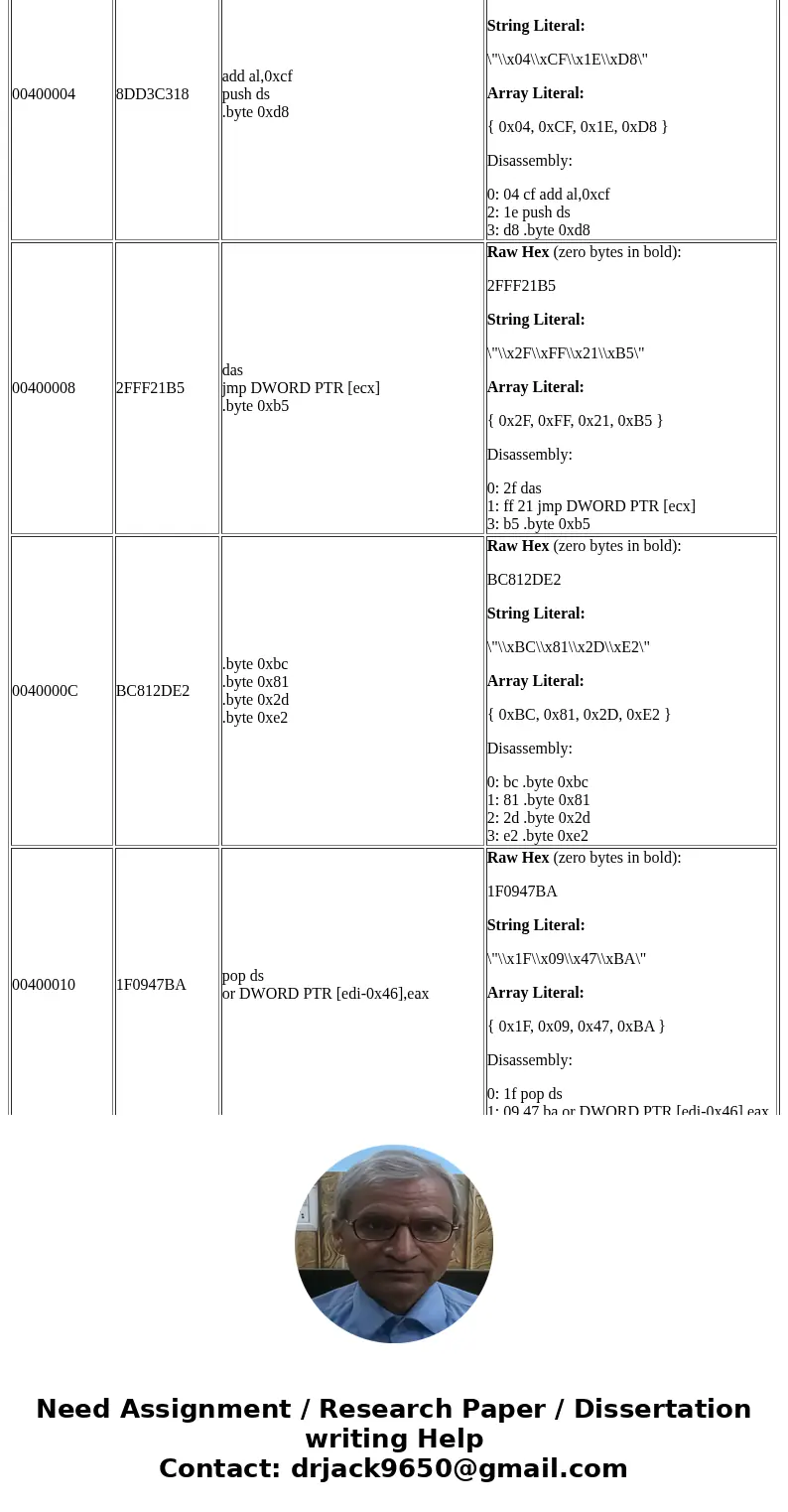
00400004
8DD3C318
00400008
2FFF21B5
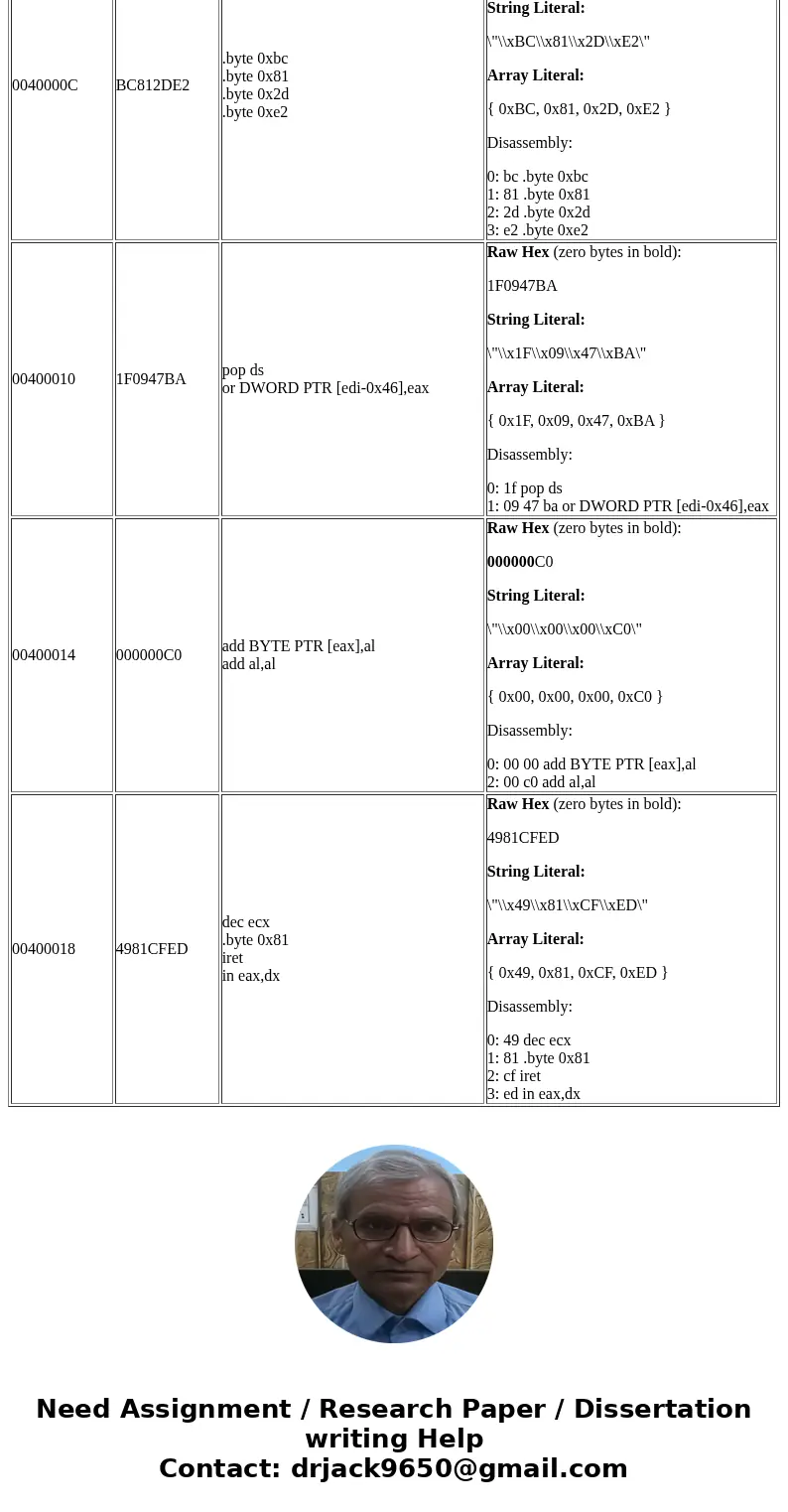
0040000C
BC812DE2
00400010
1F0947BA
00400014
000000C0
00400018
4981CFED
| Address | Instruction | Assembly Language Instruction |
| 00400000 | 04CF1ED8 | |
| 00400004 | 8DD3C318 | |
| 00400008 | 2FFF21B5 | |
| 0040000C | BC812DE2 | |
| 00400010 | 1F0947BA | |
| 00400014 | 000000C0 | |
| 00400018 | 4981CFED |
Solution
Address
Instruction
Assembly Language Instruction
00400000
04CF1ED8
add al,0xcf
push ds
.byte 0xd8
Raw Hex (zero bytes in bold):
04CF1ED8
String Literal:
\"\\x04\\xCF\\x1E\\xD8\"
Array Literal:
{ 0x04, 0xCF, 0x1E, 0xD8 }
Disassembly:
0: 04 cf add al,0xcf
2: 1e push ds
3: d8 .byte 0xd8
00400004
8DD3C318
add al,0xcf
push ds
.byte 0xd8
Raw Hex (zero bytes in bold):
04CF1ED8
String Literal:
\"\\x04\\xCF\\x1E\\xD8\"
Array Literal:
{ 0x04, 0xCF, 0x1E, 0xD8 }
Disassembly:
0: 04 cf add al,0xcf
2: 1e push ds
3: d8 .byte 0xd8
00400008
2FFF21B5
das
jmp DWORD PTR [ecx]
.byte 0xb5
Raw Hex (zero bytes in bold):
2FFF21B5
String Literal:
\"\\x2F\\xFF\\x21\\xB5\"
Array Literal:
{ 0x2F, 0xFF, 0x21, 0xB5 }
Disassembly:
0: 2f das
1: ff 21 jmp DWORD PTR [ecx]
3: b5 .byte 0xb5
0040000C
BC812DE2
.byte 0xbc
.byte 0x81
.byte 0x2d
.byte 0xe2
Raw Hex (zero bytes in bold):
BC812DE2
String Literal:
\"\\xBC\\x81\\x2D\\xE2\"
Array Literal:
{ 0xBC, 0x81, 0x2D, 0xE2 }
Disassembly:
0: bc .byte 0xbc
1: 81 .byte 0x81
2: 2d .byte 0x2d
3: e2 .byte 0xe2
00400010
1F0947BA
pop ds
or DWORD PTR [edi-0x46],eax
Raw Hex (zero bytes in bold):
1F0947BA
String Literal:
\"\\x1F\\x09\\x47\\xBA\"
Array Literal:
{ 0x1F, 0x09, 0x47, 0xBA }
Disassembly:
0: 1f pop ds
1: 09 47 ba or DWORD PTR [edi-0x46],eax
00400014
000000C0
add BYTE PTR [eax],al
add al,al
Raw Hex (zero bytes in bold):
000000C0
String Literal:
\"\\x00\\x00\\x00\\xC0\"
Array Literal:
{ 0x00, 0x00, 0x00, 0xC0 }
Disassembly:
0: 00 00 add BYTE PTR [eax],al
2: 00 c0 add al,al
00400018
4981CFED
dec ecx
.byte 0x81
iret
in eax,dx
Raw Hex (zero bytes in bold):
4981CFED
String Literal:
\"\\x49\\x81\\xCF\\xED\"
Array Literal:
{ 0x49, 0x81, 0xCF, 0xED }
Disassembly:
0: 49 dec ecx
1: 81 .byte 0x81
2: cf iret
3: ed in eax,dx
| Address | Instruction | Assembly Language Instruction | Explaination |
| 00400000 | 04CF1ED8 | add al,0xcf | Raw Hex (zero bytes in bold): 04CF1ED8 String Literal: \"\\x04\\xCF\\x1E\\xD8\" Array Literal: { 0x04, 0xCF, 0x1E, 0xD8 } Disassembly: 0: 04 cf add al,0xcf |
| 00400004 | 8DD3C318 | add al,0xcf | Raw Hex (zero bytes in bold): 04CF1ED8 String Literal: \"\\x04\\xCF\\x1E\\xD8\" Array Literal: { 0x04, 0xCF, 0x1E, 0xD8 } Disassembly: 0: 04 cf add al,0xcf |
| 00400008 | 2FFF21B5 | das | Raw Hex (zero bytes in bold): 2FFF21B5 String Literal: \"\\x2F\\xFF\\x21\\xB5\" Array Literal: { 0x2F, 0xFF, 0x21, 0xB5 } Disassembly: 0: 2f das |
| 0040000C | BC812DE2 | .byte 0xbc | Raw Hex (zero bytes in bold): BC812DE2 String Literal: \"\\xBC\\x81\\x2D\\xE2\" Array Literal: { 0xBC, 0x81, 0x2D, 0xE2 } Disassembly: 0: bc .byte 0xbc |
| 00400010 | 1F0947BA | pop ds | Raw Hex (zero bytes in bold): 1F0947BA String Literal: \"\\x1F\\x09\\x47\\xBA\" Array Literal: { 0x1F, 0x09, 0x47, 0xBA } Disassembly: 0: 1f pop ds |
| 00400014 | 000000C0 | add BYTE PTR [eax],al | Raw Hex (zero bytes in bold): 000000C0 String Literal: \"\\x00\\x00\\x00\\xC0\" Array Literal: { 0x00, 0x00, 0x00, 0xC0 } Disassembly: 0: 00 00 add BYTE PTR [eax],al |
| 00400018 | 4981CFED | dec ecx | Raw Hex (zero bytes in bold): 4981CFED String Literal: \"\\x49\\x81\\xCF\\xED\" Array Literal: { 0x49, 0x81, 0xCF, 0xED } Disassembly: 0: 49 dec ecx |
 Homework Sourse
Homework Sourse